Executives confront a convergence of security dominance, traffic distortion, and compliance costs.
- Cloudflare holds 82.16% of the global Distributed Denial of Service (DDoS) and bot protection market, according to ElectroIQ (2025). This level of control redefines how enterprises approach scraping, data access, and infrastructure resilience.
- The financial scale reinforces this dominance. Cloudflare’s Q2 2025 financials report $512.3 million in quarterly revenue, driving annualized revenue beyond $2 billion.
- Companies Market Cap (August 2025) values the company at €57.74 billion, ranking it as the 318th most valuable business worldwide.
- Web scraping markets expand in parallel. Business Research Insights (2025) forecasts a $10.44 billion market by 2025. The spread highlights both robust demand and volatility in adoption trajectories, often encompassing specialized data collection alongside traditional web methods.
- Traffic dynamics add pressure. The Thales/Imperva Bad Bot Report (2025) finds 51% of global web traffic is now bot-driven, with malicious actors responsible for 37%. Such trends raise compliance costs and force more sophisticated detection evasion.
Taken together, market share, traffic distortion, and growth projections clarify why Cloudflare sits at the center of enterprise scraping challenges. The following map condenses these dynamics into a single view.
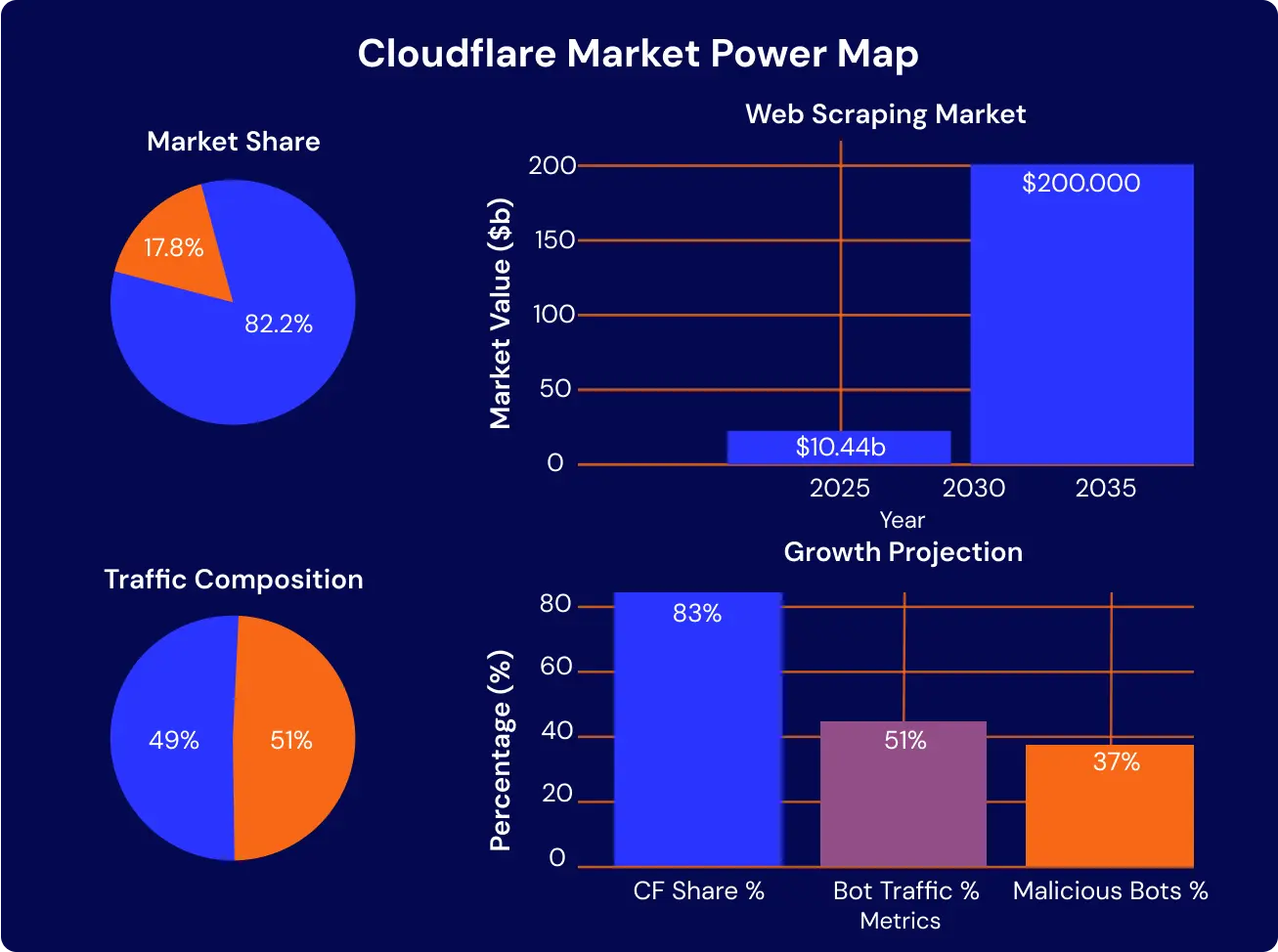
The Cloudflare Market Power Map demonstrates the convergence of scale, security dominance, and traffic complexity that executives must address when designing compliant bypass strategies.
The financial impact of breaches compounds the risk. The IBM 2025 report calculates $4.88 million average losses per incident, climbing to $6.08 million for financial institutions. Regulatory costs amplify the burden: CookieYes (2025) estimates annual GDPR compliance at €1,000–€50,000 for SMEs, with several million for large enterprises.
Together, these signals frame the stakes clearly: bypassing Cloudflare in 2025 is not a technical maneuver alone. It is a financial and strategic decision, balancing access against risk, compliance, and margin protection.
Introduction: Why Cloudflare Bypass Matters
Cloudflare dominates the internet’s defensive perimeter. The platform protects more than 20% of global web traffic with detection systems that classify every incoming request. Executives pursuing competitive intelligence often meet an invisible barrier: pages locked behind active bot screening and fingerprint checks. Facing such barriers is a critical aspect of understanding the fundamental challenges in web scraping today.
The OECD’s Government at a Glance 2025 highlights the strategic weight of open data in policy and business development. For enterprises, restricted access means delayed decisions and incomplete signals. A blocked data feed can stall pricing moves, inventory models, or risk assessments that depend on real-time flows.
Security layers are not static. Cloudflare bypass strategies that worked last year fail quickly as scoring engines adapt to new signatures. Detection models process billions of daily interactions, refining trust ratings for each browser or device. This massive processing capability is powered by big data analytics. Executives, therefore, require methods that combine legal compliance with operational resilience. Without that combination, attempts at scraping Cloudflare-protected website content introduce more risk than insight.
The strategic imperative is clear. Organizations cannot afford to ignore Cloudflare, nor can they operate outside the regulatory perimeter. Every bypass Cloudflare plan must demonstrate two things: protection of business continuity and adherence to evolving privacy law. The following sections unpack the architecture, tools, and compliance structures that define sustainable approaches.
Cloudflare’s Multi-Layered Security Architecture
Cloudflare deploys a blended security stack. Passive checks review IP reputations, request headers, and TLS handshakes. Active checks introduce JavaScript puzzles, CAPTCHA, and behavior tracking. Together, these mechanisms create a shifting defense system that reduces automated access while preserving legitimate traffic.
Cloudflare’s defensive layers interact as a flow, where passive checks filter first, active challenges escalate risk scores, and a central trust engine determines outcomes. The following schema illustrates this progression.
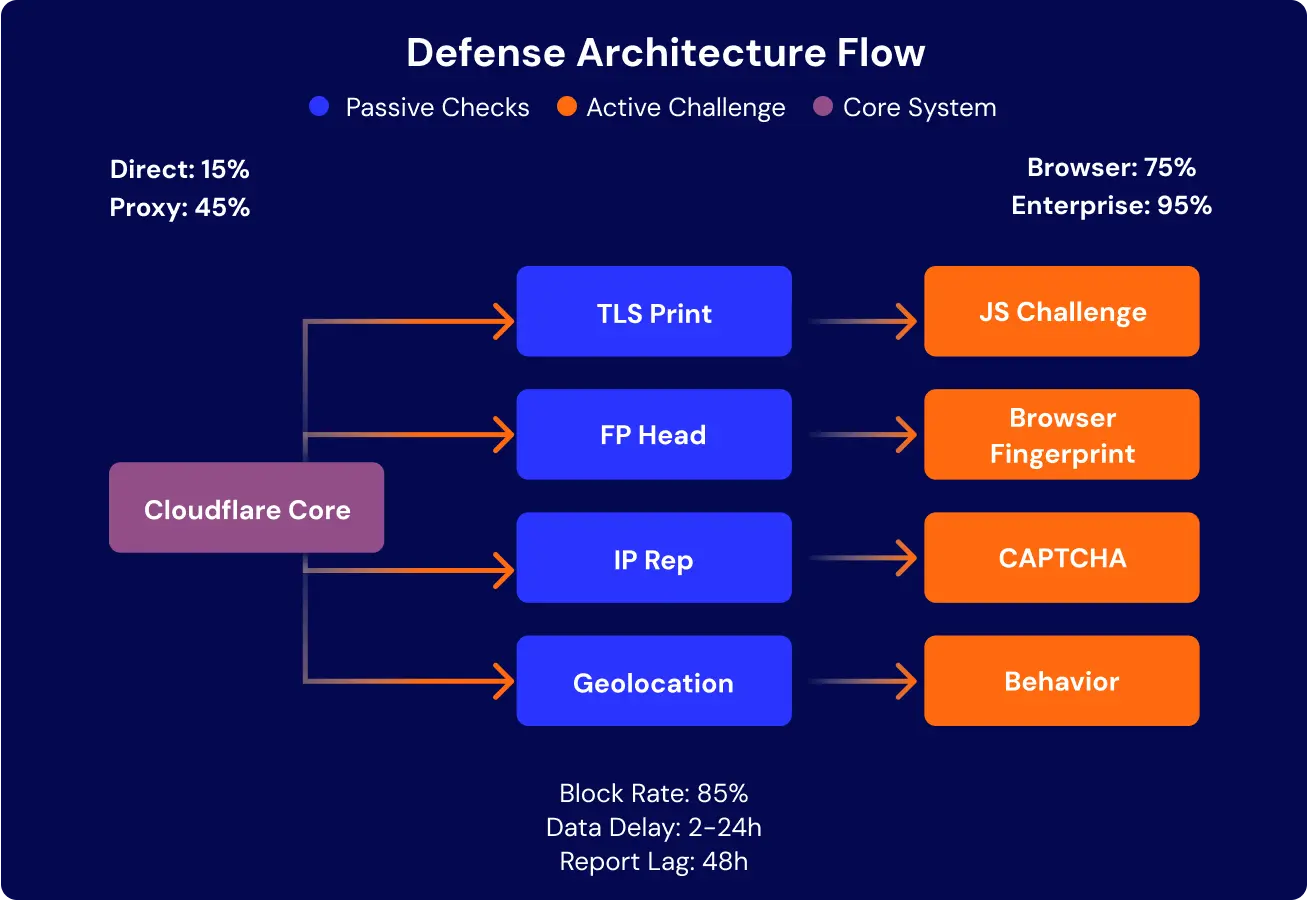
The Defense Architecture Flow highlights why bypass strategies must counter both passive fingerprinting and active behavioral tests. Ignoring either layer leads to inflated block rates and distorted datasets.
The Cloudflare Bot Management documentation explains how these engines classify traffic. Requests flagged as suspicious either face challenge pages or receive outright blocking. For executives, the consequence is measurable: blocked data streams translate into slower reporting cycles and weaker margin defense.
TLS fingerprinting illustrates the sophistication of modern defenses. Research on JA3 and JA4 methods shows how servers can identify client software with near-unique precision. A mismatched signature immediately signals automation. The result is higher block rates, forcing systems to retry requests and inflate infrastructure costs.
JavaScript fingerprinting adds another barrier. Cloudflare collects data on browser versions, installed fonts, screen resolution, and hardware identifiers. These techniques are increasingly sophisticated, mirroring the strict controls outlined in any effective Google fingerprinting policy documentation.
Cloudflare bypass strategies must therefore account for fingerprint precision. Ignoring these realities results in wasted spend, compliance exposure, and degraded analytic models. Secure approaches show how to bypass Cloudflare protection without crude tricks. They instead orchestrate browser automation and proxy management in ways that align with both technical resilience and regulatory boundaries.
Executives evaluating bypass strategies face asymmetric trade-offs. Each method scores differently across effectiveness, scalability, legal risk, and detection exposure. No universal option exists—architecture must match enterprise tolerance for cost and compliance overhead.
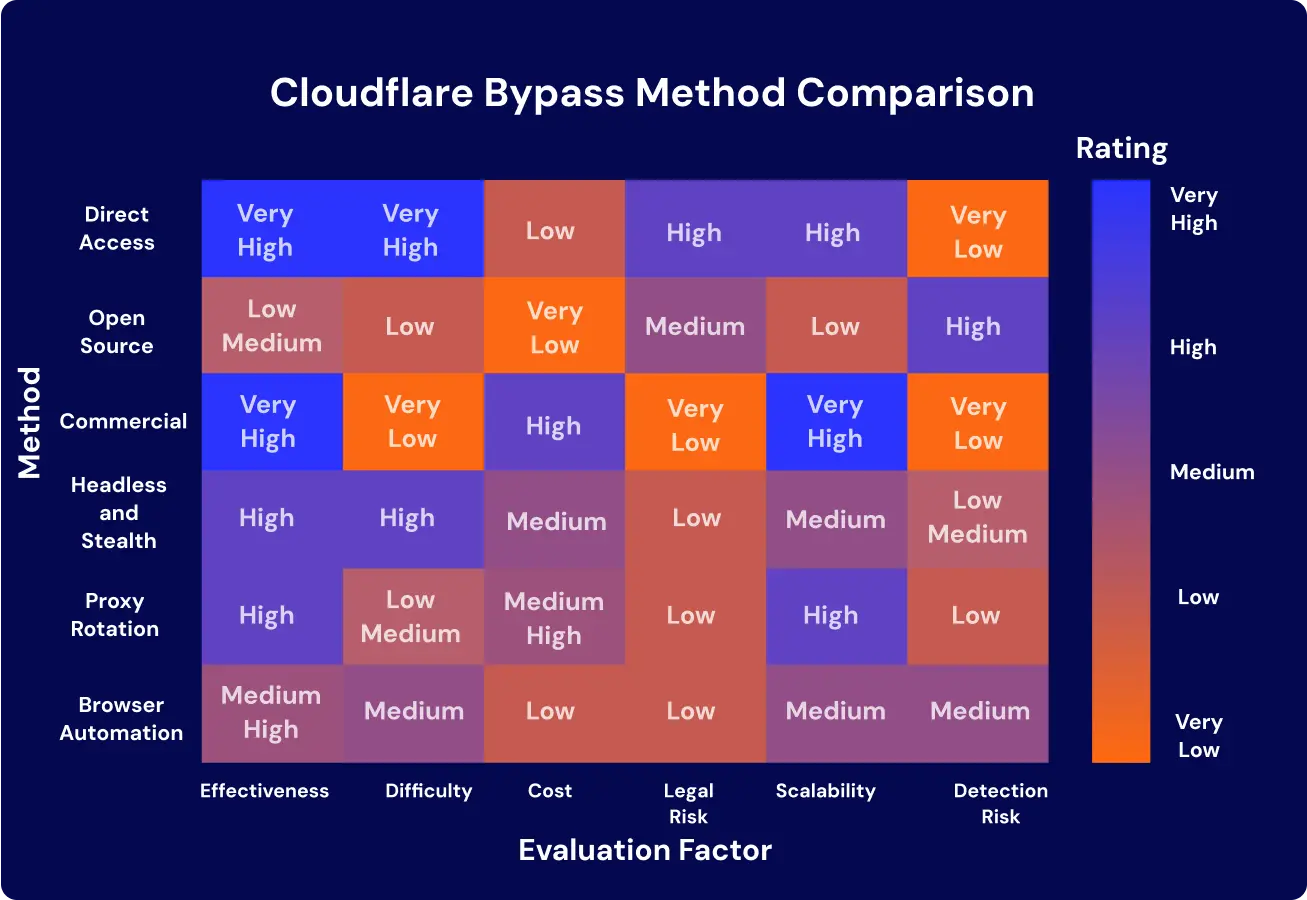
The comparison highlights how direct access offers strong effectiveness but unsustainable risk, while proxy rotation and headless stealth methods strike a balance between scale and compliance. Commercial providers deliver simplicity but introduce vendor lock-in and budget pressure.
Secure Approaches to Bypassing
Executives face a practical dilemma. Data streams vital for pricing, inventory, and risk modeling often sit behind layered security walls. Building sustainable access requires methods that withstand detection cycles, scale efficiently, and remain compliant. The following three approaches—browser automation, proxy orchestration, and behavioral mimicry—form the operational core of any resilient bypass Cloudflare strategy.
Browser Automation and Stealth
Automation frameworks replicate genuine browsing sessions. Selenium, Playwright, and Puppeteer lead the field, while emerging tools like Camoufox extend reach with enhanced fingerprint controls. Each framework supports JavaScript execution, an essential requirement for scraping Cloudflare-protected website environments that depend on active challenge validation.
Stealth plugins reduce detection signatures. Undetected Chrome drivers or specialized plugins, such as puppeteer-extra-plugin-stealth and its Playwright ports, or manual browser launch settings, conceal automation flags that Cloudflare inspects. Playwright does not have built-in stealth settings; additional plugins or advanced configuration improve covertness.
The ACM’s Transactions on AI Security and Privacy launch underscores why this matters. The journal highlights how evolving detection systems focus on behavioral anomalies rather than surface identifiers. Executives should note the cost implication: every failed session increases server loads and inflates infrastructure spend.
Modern automation goes further. Humanization modules generate natural cursor curves, varied click timing, and scrolling depth aligned with real usage. These refinements lower block rates and preserve session continuity. Without them, repeated challenge failures distort collected datasets, forcing data leads to recalibrate analytic models at significant expense. When building these complex pipelines internally, organizations must choose the best operational framework, often debating the merits of PHP vs Python for web scraping based on ecosystem maturity and performance needs.
Anti-Detect Browsers
Beyond plugins, specialized anti-detect browsers mask digital fingerprints at scale. Open-source solutions like Camoufox serve advanced users, while proprietary tools such as Octo, Indigo, Multilogin, and Gologin provide commercial alternatives. These browsers modify Canvas/WebGL fingerprints, WebRTC leaks, fonts, and user agents, making them heavier but more resilient options compared to plugins.
It is important to distinguish roles. Selenium, Playwright, and Puppeteer are frameworks that control browsers, while stealth plugins and anti-detect browsers are masking tools that make the browser appear to be a regular, human-operated environment rather than an automated one.
Proxy Orchestration
Proxy infrastructure determines scale. Residential IPs carry higher trust scores than datacenter addresses, reducing the frequency of block events for executives, which translates into uninterrupted access and stable refresh cycles. Effective orchestration rotates IPs while preserving session persistence, ensuring authentication cookies remain valid across extended capture windows. For these high-scale, continuous operations, a disciplined approach to proxy rotation for web scraping is necessary to maximize uptime.
Geographic distribution adds another layer. Requests routed through region-specific IPs align with local regulations and avoid jurisdictional mismatches. The ISO 27001 risk management framework stresses the importance of geographic compliance. Enterprises following these controls reduce exposure to cross-border data restrictions, cutting regulatory risk before it translates into financial penalties.
Orchestration must be intelligent. Blind rotation creates detection patterns. Coordinated systems pace requests, align them with browsing logic, and balance throughput against challenge risk. Executives should treat this as more than infrastructure hygiene. Poor proxy management triggers repeated bans, delaying analysis cycles and eroding margin gains that depend on real-time intelligence. In short, how to get past Cloudflare without these controls is operationally untenable.
Session Warming and Behavior Mimicry
Cloudflare’s trust engine scores sessions dynamically. Systems that leap directly to high-value pages raise suspicion. Session warming counters this by staging visits. Traffic begins at the homepage, flows into category sections, and then navigates to target content. This staged approach builds trust gradually, lowering challenge frequency. This staged approach is especially vital for platforms like Booking.com, where detailed navigation is crucial for effective scraping Booking.com data collection.
Behavioral mimicry amplifies the effect. Naturalized scrolling, pauses between page interactions, and varied dwell time create the appearance of genuine browsing. Research on bot detection in social media concludes that statistical anomalies in navigation patterns remain a primary detection signal arXiv. Executives should translate that insight into a direct consequence: automated systems failing to mirror human rhythm face higher rejection rates, undermining the reliability of competitive benchmarks.
Cookie and session management sustain continuity. Tokens secured during warming phases extend across multiple requests, maintaining the appearance of an unbroken session. Bypassing Cloudflare requires more than technical persistence. It demands behavioral realism that keeps scoring models aligned with authentic user activity. How to get around Cloudflare without this realism results in erratic datasets that mislead forecasting systems and disrupt pricing accuracy.
Secure bypass operations depend on layered execution. Browser automation delivers capability, proxy orchestration provides scale, and behavior mimicry sustains trust. Executives should view these methods not as technical tricks but as structural safeguards. Together they reduce infrastructure waste, preserve data accuracy, and protect compliance boundaries—all essential to maintaining decision speed under Cloudflare’s expanding defensive reach.
Executives require more than technical explanation; they need a comparative view that clarifies trade-offs across cost, compliance, and resilience. The following table condenses the three primary Cloudflare bypass methods into a format that highlights their operational strengths and structural risks. This view accelerates board-level decisions by exposing where investment supports resilience and where shortcuts invite liability.
| Method | Strengths | Limitations / Risks |
| Browser automation | Browser automation Executes JavaScript, replicates authentic browsing, lowers block rates with stealth plugins and humanization modules. |
High infrastructure load; frequent updates required; failed sessions inflate cost and distort datasets. |
| Proxy orchestration | Maintains geographic compliance, enables session persistence, and reduces block frequency through residential IP rotation. | Proxy costs rise quickly at scale; blind rotation triggers detection patterns without intelligent orchestration. |
| Behavior mimicry | Builds trust through staged navigation, naturalized scrolling, dwell time variation, and cookie continuity. | Complex to design and maintain; weak mimicry produces erratic datasets that undermine pricing and forecasting models. |
The comparison clarifies why no single method suffices on its own. Browser automation secures capability, proxy orchestration ensures scale, and behavioral mimicry sustains trust. Enterprises that orchestrate these approaches together build resilient access pipelines, while those that rely on one alone face rising costs, compliance pressure, and fragile outcomes.
Compliance-First Bypass Strategies
Every Cloudflare bypass attempt exposes the organization to legal, financial, and technical risks. Sustainable access requires governance structures that integrate regulatory safeguards with operational resilience.
GDPR and Privacy
European regulators frame scraping within privacy law. The 2025 stresses that lawful collection depends on legitimate interest, strict minimization, and anonymization. Executives who ignore these safeguards face fines up to four percent of global turnover. Systems that pseudonymize or strip identifiers during capture preserve value while lowering liability. Legal teams must also document why processing qualifies as legitimate interest, providing assessments that quantify risks and define safeguards. Without this discipline, Cloudflare bypass operations escalate into legal confrontation. This is why obtaining clarity on all rules for GDPR web scraping must precede technical implementation.
Robots.txt and Terms of Service
Automated sessions must respect declared boundaries. Robots.txt files specify allowances, crawl delays, and restricted directories. Terms of service reinforce these limits. Disregarding them accelerates detection and invites legal or contractual disputes. Executives should enforce controlled pacing and avoid restricted endpoints as proof of good faith. This discipline converts compliance into insulation against disputes. In general, understanding whether is web scraping legal requires a comprehensive review of these public-facing documents alongside jurisdictional laws.
Risk Categories
Legal exposure compounds when technical risks overlap with regulatory failures. The following heatmap quantifies potential cost ranges, from intellectual property disputes to GDPR violations, mapped against system weaknesses.
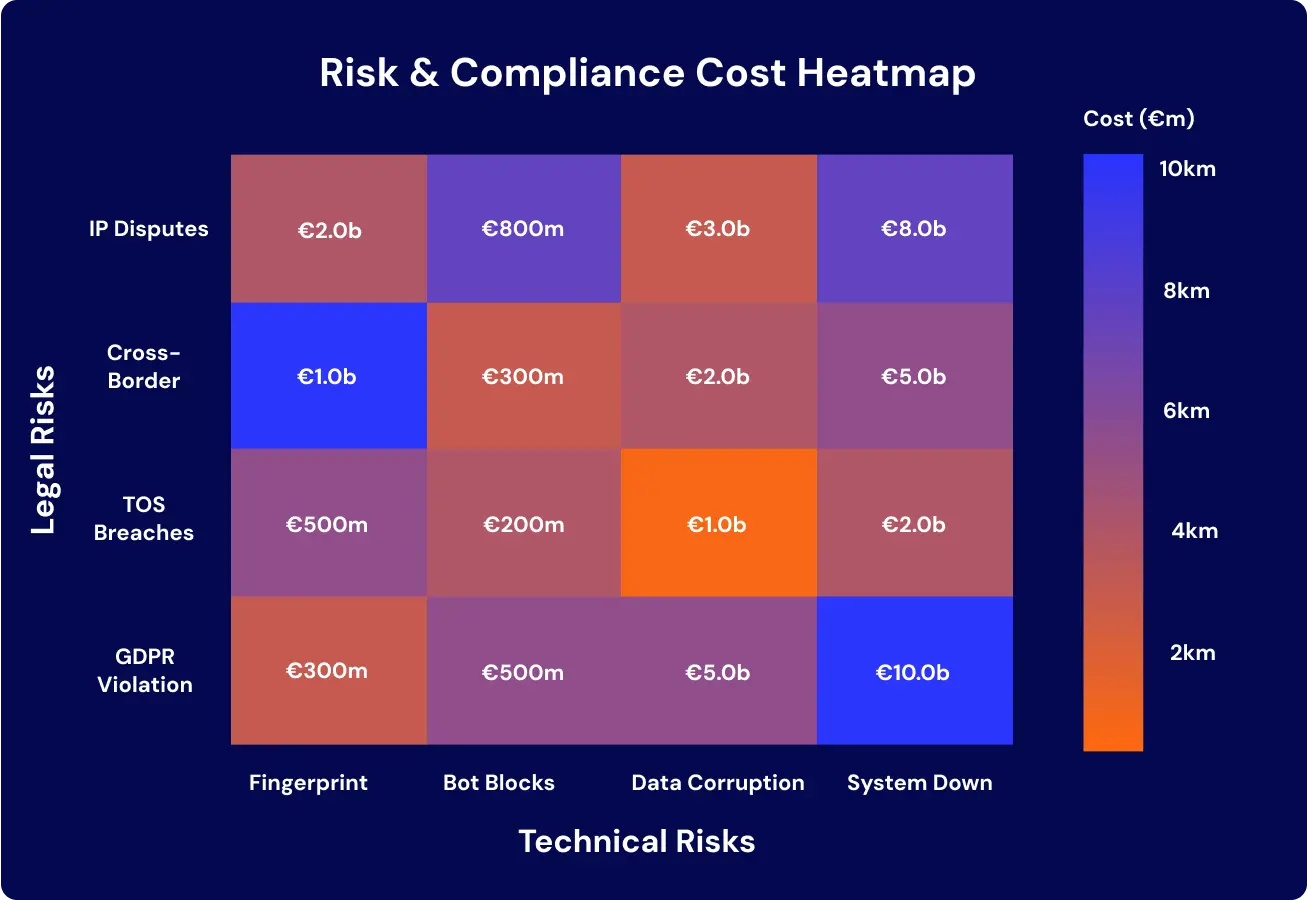
The heatmap illustrates how unmanaged risks escalate into billion-euro liabilities. Governing systems reduce exposure by centralizing controls, converting compliance from overhead into resilience.
Another risk is technical fragility. Both dimensions require disciplined assessment before any bypass Cloudflare strategy proceeds. Treating risk as architecture, not an afterthought, ensures that data pipelines survive regulatory and technical shocks.
Commercial and Hybrid Solutions
Technology choice determines operational stability. Many internal teams attempt to engineer Cloudflare bypass systems from scratch. That approach often underestimates cost, exposes compliance gaps, and risks frequent disruption. Executives evaluating alternatives should weigh the resilience of enterprise-grade platforms against the flexibility of hybrid strategies.
Enterprise-Grade Platforms
Professional scraping APIs package resilience. Services handle proxy rotation, fingerprint management, and CAPTCHA solving as managed functions. The European Commission’s delegated act under the Digital Services Act highlights the policy direction. Regulators now expect researchers and businesses to access protected content through structured, compliant channels. Many turn to the best web scraping companies to manage this complexity, ensuring predictable uptime and technical evolution.
These platforms align with that shift. Contractual agreements, service-level guarantees, and dedicated compliance support reduce uncertainty. Executives gain predictable uptime and clearer legal positioning. The financial case is direct: bypass Cloudflare tasks, shift from engineering burden to subscription cost, freeing resources for higher-value analysis. This outsourcing is often handled by a dedicated web scraping company that offers service-level agreements on data access.
Cost efficiency matters as well. Internal systems often require constant patching as detection evolves. By contrast, commercial platforms distribute these costs across multiple clients, lowering per-user expense. For mission-critical access, how to bypass Cloudflare decisions increasingly converges on outsourcing rather than building.
Hybrid Approaches
Not every use case warrants commercial tooling. Many enterprises adopt hybrid models: internal systems manage routine capture, while third-party APIs cover high-value or high-risk endpoints. This mix balances control with resilience.
Budget allocation drives architecture. Internal tools maintain low-cost pipelines for standardized tasks. Commercial services absorb complexity where compliance or detection pressure spikes. Executives should frame the consequence clearly: hybrid models preserve agility, reduce fixed costs, and maintain operational certainty when scraping Cloudflare protected website environments. The ultimate goal is to integrate all these data streams reliably into the core big data pipeline architecture for immediate analysis.
Compliance is not optional. Governance, robots.txt respect, and structured risk frameworks convert bypass Cloudflare operations from liability into a durable capability. Commercial and hybrid solutions then scale this capability into resilient infrastructure.
Executives who combine these pillars protect margin, maintain decision speed, and operate with legal defensibility in a tightening regulatory climate.
Best Practices and Governance
Executives must convert bypass operations into governed systems. Ad hoc methods might achieve temporary access, but only structured practices ensure repeatable, compliant performance. Three disciplines—code standards, governance, and continuous improvement—anchor this conversion.
Technical Standards
Development discipline underpins reliability. Code must be documented, tested, and version-controlled to maintain traceability. Monitoring and alerting systems then provide visibility into session failures, error clusters, and access disruptions. This visibility translates into faster recovery times and reduced revenue impact.
Bypass Cloudflare efforts without these standards drift into fragile, opaque scripts that collapse under scrutiny. Executives should enforce technical rigor as an operational mandate, not an optional enhancement.
Organizational Governance
Cross-functional coordination aligns legal, technical, and business teams. Regular governance reviews ensure that data collection strategies match both compliance rules and revenue goals. Training programs extend awareness, equipping engineers with the context to implement scraping Cloudflare-protected website techniques responsibly. This governance is especially vital in competitive industries where a targeted web scraping solution for tackling unfair competition may require swift, legally defensible data collection.
The World Economic Forum’s Global Cybersecurity Outlook 2025 highlights governance gaps as a key source of enterprise risk. For executives, the consequence is direct: governance failures increase exposure to cyber incidents, while coordinated oversight reduces disruption and preserves margin.
Bypass strategies must evolve. Detection methods change quarterly, and legal environments shift with equal speed. Systems that lack review cycles become obsolete, leaving executives dependent on outdated tactics.
Summary and Executive Takeaways
Executives face a dual imperative: maintain compliant access while preserving technical capability. Cloudflare bypass strategies that succeed combine automation, proxy orchestration, and behavioral mimicry with documented safeguards and risk frameworks. The consequence is measurable. Organizations achieve uninterrupted data flows, lower legal exposure, and faster decision velocity.
Compliance anchors capability. GDPR alignment, robots.txt respect, and enterprise risk management transform access from liability into infrastructure. Risk monitoring ensures that how to bypass Cloudflare methods evolve with regulation and detection shifts. Without this balance, operations collapse under penalties or technical blocks. This capability is extended by specialized offerings, such as mobile app scraping services, to ensure all data vectors are covered.
Strategic direction must therefore emphasize resilience. Commercial services provide scale, hybrid models preserve agility, and governance ensures defensibility. The ETSI Security Conference 2025 highlights how integrated standards now shape enterprise automation. For executives, the takeaway is clear: Cloudflare bypass becomes sustainable only when technical excellence operates inside legal guardrails. To maintain price advantage and inventory accuracy, executives rely heavily on ecommerce data scraping services that demonstrate high resilience against anti-bot systems.
FAQ
-
What is the safest first step to bypass Cloudflare for enterprise scraping?
Executives begin with a controlled proof of concept using browser automation paired with legal pre-review. This staged entry optimizes proxy expenditure by validating the approach before scaling and lowers the likelihood of detection spikes. While browser automation consumes significantly more traffic than lightweight request methods, proof-of-concept runs prevent larger waste by avoiding full-scale investment into ineffective strategies. A measured start ensures infrastructure remains stable while compliance teams validate risk tolerance. The outcome is a defensible pathway that balances data access with operational safety.
-
Is scraping Cloudflare-protected websites legal under GDPR and global privacy laws?
Legality depends on basis, safeguards, and intent. GDPR permits scraping under legitimate interest if data is anonymized, minimized, and supported by documented assessments. U.S. and Asian jurisdictions apply parallel conditions, with stricter oversight on consumer identifiers. Executives who apply pseudonymization and maintain audit trails preserve defensibility under regulator inquiry.
-
How much does Cloudflare bypass cost compared to commercial data APIs?
Internal pipelines require proxy rotation, fingerprint controls, and continuous updates, driving recurring engineering and infrastructure costs. Commercial APIs shift these costs into subscription fees, which scale predictably but introduce vendor lock-in. Hybrid models combine both: routine capture handled internally, high-value endpoints outsourced. Analysts also debate how to bypass Cloudflare block without inflating compliance overhead.
-
How often do bypass methods fail, and what happens when they do?
Failure is inevitable as Cloudflare adapts signatures weekly. Teams explore how to bypass Cloudflare blocked flows when typical block rates range between 10–20 percent without advanced orchestration, inflating retries and infrastructure costs. Enterprises counter this with fallback pathways, such as reserve proxies or diversified capture routes. These controls protect continuity and keep reporting cycles aligned with decision velocity.
-
Who in the enterprise is accountable if a Cloudflare bypass raises compliance issues?
Responsibility sits across legal, data governance, and security teams. Legal validates jurisdictional fit, data governance ensures safeguards, and the CISO oversees infrastructure exposure. Boards increasingly demand that any method labeled how to bypass Cloudflare security be documented as an auditable framework, not a tactical workaround. Clear accountability preserves both executive defensibility and organizational margin resilience.






