
The Client Story
A European cybersecurity provider defended thousands of enterprise clients against advanced attacks. Its Security Operations Center ingested petabytes of logs and billions of daily events across networks, endpoints, cloud platforms, and threat feeds. The scale produced three acute risks.
Analysts drowned in false positives, heightening burnout and missed threats. Legacy detection methods, relying heavily on rules, struggled against multi-stage attacks unfolding over weeks, contributing heavily to the noise. Fragmented tools blocked hunters from maintaining a unified adversary view.
| Industry: | Cybersecurity |
|---|---|
| Cooperation: | 2025 |
| Location: | Europe |
“As a SOC director in cybersecurity, I need signals I can act on. The platform reduced noise to the point where my team finally focuses only on genuine incidents.” — SOC Director, Cybersecurity
“As a head of engineering in security services, I measure value in cycles and cost. Automated pipelines removed repetitive work and gave us time to design stronger defense models.” — Head of Engineering, Cybersecurity
AI Security Analytics Replaces Legacy Risk Model
The provider’s massive data volume and fragmented security tooling created critical operational risks. Analysts drowned in false alerts. The reliance on legacy detection methods—primarily rules and signatures—couldn’t effectively manage the complexity and stealth of modern, multi-stage cyberattacks. This resulted in thousands of daily false positives, raising operational costs and fueling analyst burnout.
Genuine threats disappeared in the noise. The priority became transitioning from a reactive, rule-centric defense to a unified, proactive, and predictive AI-driven security model. This shift cut operational costs by 18% within one year.
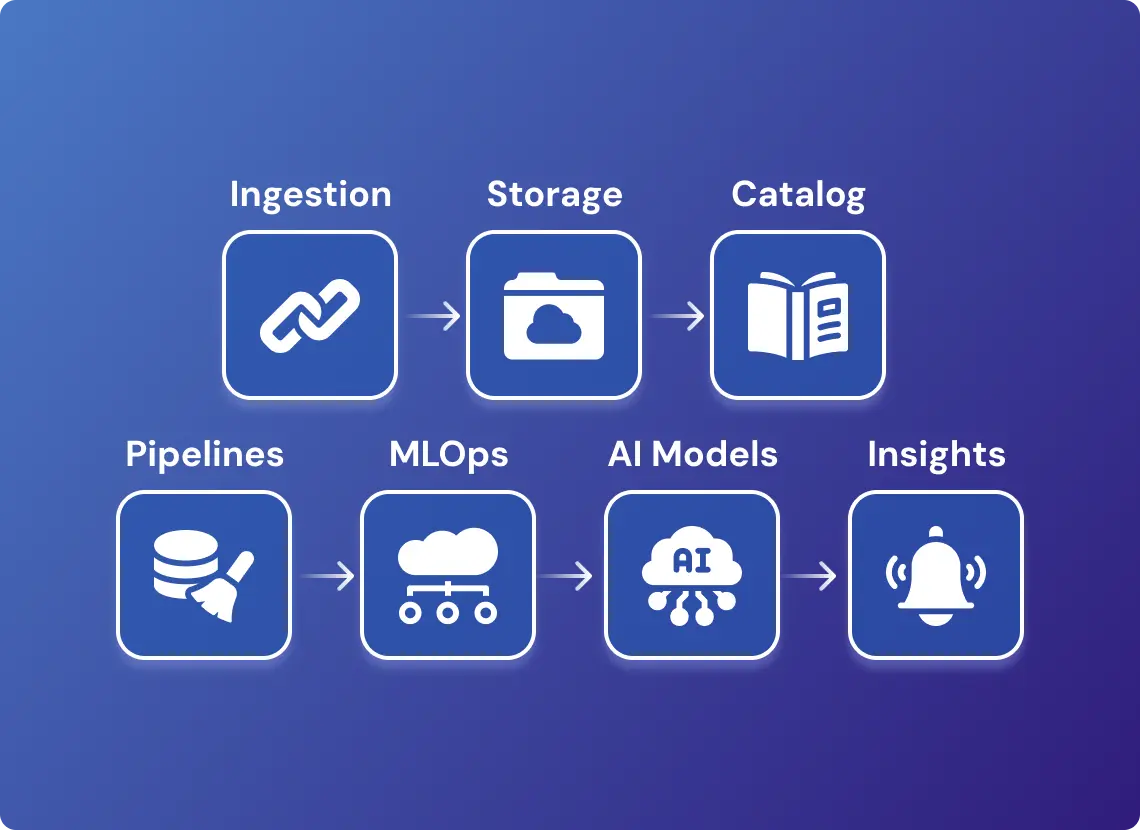
Unified Threat Intelligence Architecture
The delivery team deployed an AI intelligence platform to centralize analytics. A unified catalog enforced governed access across logs and curated intelligence, acting as a central metadata store. Governed access included role-based permissions, audit logging, and policy-driven visibility, ensuring compliance while preserving analyst speed.
Clear lineage from raw input to final insight simplified audits and strengthened governance. Declarative pipelines, built on Apache Spark and Flink, processed streams at petabyte scale in real time. This declarative method lets engineers define desired outcomes (“what”) instead of coding every step (“how”), which cuts maintenance overhead.
Supporting infrastructure anchored the approach: data lakes stored raw logs under governance policies, while MLOps pipelines managed model versioning, CI/CD, and rollback across environments. This ensured continuity when new models were deployed and stabilized performance during production shifts.
Predictive models created the core advance:
- Anomaly detectors scanned user and network behavior to surface compromised accounts.
- AI triage separated genuine incidents from noise, reducing alerts by 85 percent.
- Threat-hunting accelerators enabled scientists to deploy new models quickly across all inputs.
We moved from reacting to alerts to anticipating adversary tactics. Predictive models now let us see faint signals of complex attacks before damage occurs.

Faster Detection, Higher Accuracy, Lower Cost
Within the first year, outcomes shifted clearly:
- 45% faster Mean Time to Detect (MTTD) critical threats, from 11 hours to under six.
- 2.5× faster deployment of threat models, closing gaps on emerging attack vectors.
- 85% fewer false positives, down from 1,200 daily spurious alerts to fewer than 200.
SOC investigations that once took days now close in under an hour. Analyst capacity remained stable, while engineering cycles redirected toward model design. Centralized flows reduced preparation time by 35% and eliminated 4–6 planned hires, resulting in an 18% decrease in operating costs.
Savings came from automating manual validation and scaling without new staff. For example, automation eliminated 1,200 analyst hours per quarter, equivalent to four full-time roles in triage. Funds shifted into proactive hunting and forensics, strengthening resilience without a new budget.

Schedule a Security Intelligence Review
Assess how unified analytics and predictive models shorten detection cycles, suppress false alerts, and preserve SOC capacity under rising attack volumes.
You have an idea?
We handle all the rest.
How can we help you?



